Despite security being a key benefit of cloud adoption, we’ve ended up with a lack of confidence in managing threats, and increasing cybersecurity incidents.
How?
In Part 1 and Part 2 of our barriers to cloud series, we addressed how the talent shortage and team misalignment were preventing companies from making the journey to the cloud.
Today, we have the privilege of speaking with Steve Teo to address the third key barrier to cloud adoption – security.
Steve is the Director of Cloud Security Engineering at Horangi, a fast-rising SaaS-focussed cybersecurity company based in Singapore, with operations in Hong Kong, Indonesia, Thailand, South Korea, the Philippines, and the U.S. This young company is one to watch, with high-profile clients like unicorns Gojek, Bukalapak, Ninja Van, ShopBack and PropertyGuru.
As a certified AWS Solutions Architect, Steve is no stranger to architecting, building and defending cloud workloads. He also serves as the leader of the AWS User Group Singapore and is globally recognized as an AWS Community Hero. So he’s pretty well-placed to tackle these cloud security FAQs.

What are the most common cybersecurity myths Singaporean businesses believe in?
There are 2 common myths that organisations buy into: one is that because they are small, they won’t be the target of a breach.
The other myth in APAC is that they believe their organisation’s sufficiently secure due to the fact that they have performed their annual penetration test.
Although running penetration tests and vulnerability assessments on a regular basis is a crucial part of maintaining security, there is an entire universe of controls and activities that businesses should be considering to bolster their defences: incident response planning, live security monitoring and response developing a comprehensive cybersecurity program.
From Horangi’s experience, many organisations do not have the capability and resources to handle these activities well, and this gets in the way of effective incident response.
Many organisations Horangi encounters handle these activities poorly or not at all, which will definitely get in the way of any effective cybersecurity incident response.
In reality, what are the most common reasons for security breaches?
In Verizon’s 2020 Data Breach Investigations Report, most attackers found success through stolen credentials procured through phishing.
Defenders have to worry about securing any and all vulnerabilities in order to fully protect a system (which is practically impossible), while attackers just have to find one single vulnerability to exploit.
Whether it is an overlooked vulnerability, user error, or even socially engineering their way in, attackers have numbers on their side.
As such, the focus has been shifted to minimizing the impact of cyber attacks when they occur through quick and accurate detection of breaches, followed by swift containment and recovery.
Is there a Cybersecurity framework for firms to practice?
Frameworks are a great place to benchmark your organisation’s capabilities and controls. When it comes to information security and cybersecurity, the most prevalent frameworks are NIST’s CSF (Cyber Security Framework) and ISO/IEC’s ISO 27001.
Both frameworks set a foundation for the secure handling of information and proper response to scenarios where that information may be compromised.
A great resource from Horangi on this topic is 13 Compliance Frameworks For Cloud-Based Organisations.
How do providers like AWS and Microsoft secure your workloads in the cloud, what is their role?
This is often a source of confusion for businesses but there’s a shared responsibility model when we are speaking of security and compliance in the cloud between vendors and organisations.
Here’s who’s in charge of what: cloud service providers (CSPs) are in charge of ‘security of the cloud’ and an organisation’s role is for the ‘security in the cloud’.
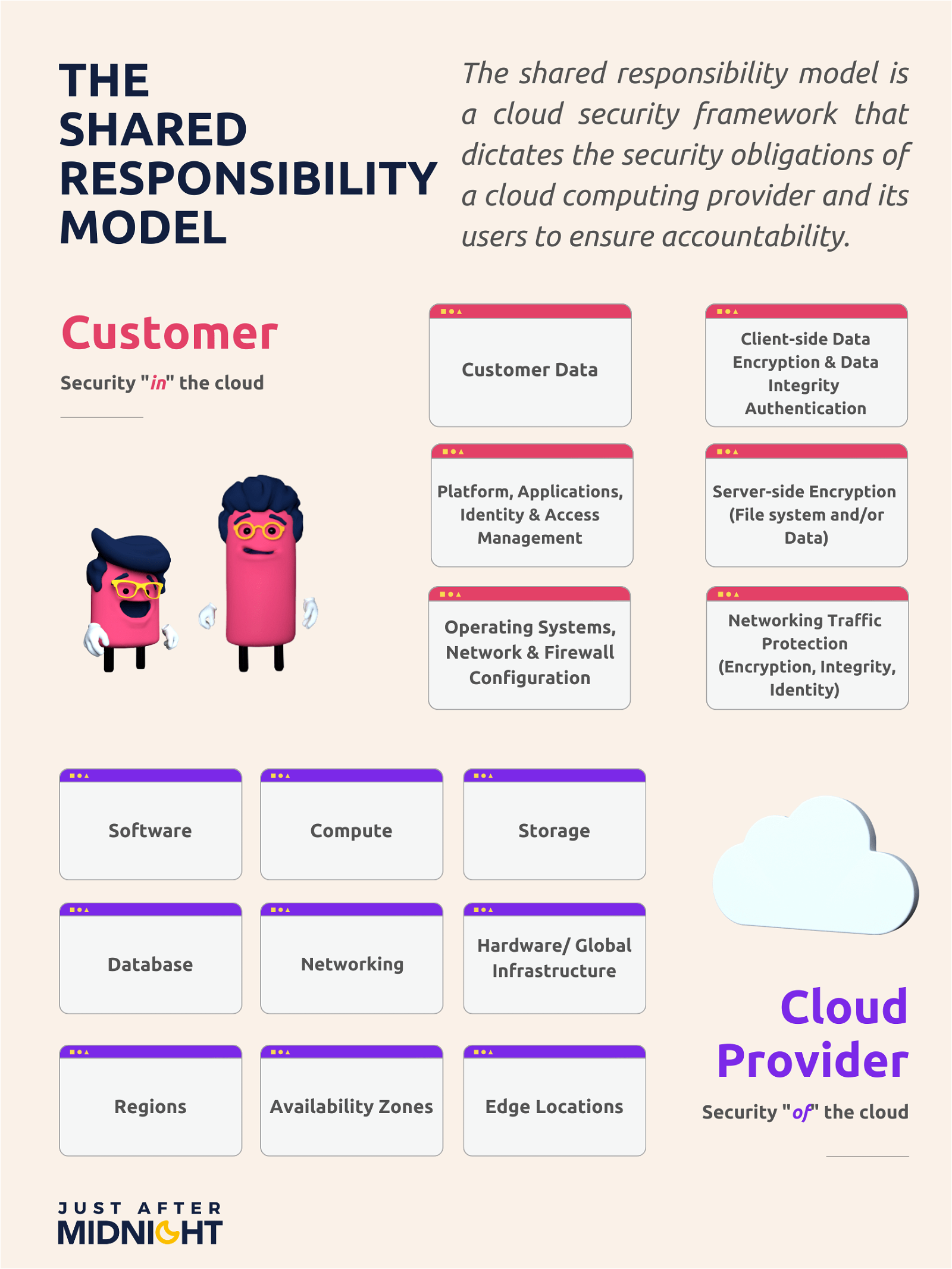
CSPs like AWS and Microsoft Azure are responsible for providing secure software, hardware, facilities and networking as part of their offering to their customers.
They know that security is key for organisations’ sense of trust when using their services, and not all customers have the access to cloud-native security tools.
Therefore, they provide a wide arsenal of native security tools so that customers have an easier time engaging in secure cloud adoption.
These service providers are frequently audited and certified according to policies and standards (across various industries) to prove that they have the technical capacity and procedures in place to protect the most sensitive business information.
And what’s the role of the organisation?
On the flip side, organisations are in charge of security in the cloud. This means whatever workloads and data that run on top of cloud services.
Though all organisations have the resources needed to conduct and uphold detailed requirements and security standards.
Here’s where an organisation can look to third-party managed cloud service providers to help them fill in the security gap.
There are third-party managed cloud service providers who focus on Vulnerability Management as a service (VMaaS) like Just After Midnight. From actively scanning your sites and assets for vulnerabilities, producing easy-to-understand, actionable tickets, and monitoring the feeds of your tech partners for patching info.
The takeaways:
- No organisation is too small, to be the target of a breach
- Passing your annual pen test isn’t an indicator that your organisation is sufficiently secure
- The most common reason for security breaches is phishing
- The most common Cybersecurity frameworks adopted as a best practice are NIST’s CSF (Cyber Security Framework) and ISO/IEC’s ISO 27001
- Security is a shared responsibility
- Cloud service providers (CSPs) are in charge of the ‘security of the cloud’ and an organisation’s role is for ‘security in the cloud’
- A Cloud Security Posture Management (CSPM) tool can help an organisation keep a watchful eye on its security by providing continuous monitoring of an organisation’s cloud environment to help identify and detect top security threats, including cloud misconfigurations, and even help organisations to stay compliant
- There are third-party managed partners who provide Vulnerability Management as a service (VMaaS)
How we can help
Offload some of the burdens of compliance and security with a cloud-native partner whose business model is built on providing superb communication, monitoring and continual improvement.
This is the third instalment of a 4-part series on barriers to cloud adoption in Singapore. You can read the following parts here: Part 1, Part 2.